Vendor Risk Management
VENDOR RISK MANAGEMENT
Visualise and manage your digital risk in one place.
Monitor, Plan, and Prioritise all your suppliers based on their Risk Severity. And keep track of all remediations, policies and team inputs all in one place, with C2’s simple 5-step process. You can reduce and mitigate your supplier chain vulnerabilities in as little as 10 minutes.
Dont hesitate, join our growing global partner community today.
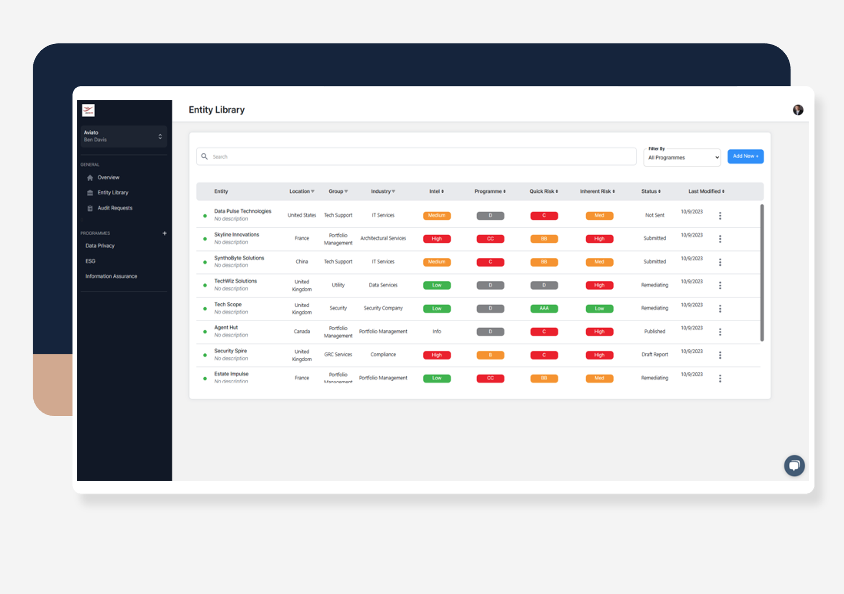
Slice your suppliers into different groups in order to be able to assess, estimate risk and apply commands and control to. By segmenting vendors into categories with similar characteristics, you can assign risk tolerances and develop roadmaps to reduce, remediate, diversify or even just monitor associated risks.
Find out what Inherent Risk is posed by a particular Vendor by analysing their policies, processes, controls, impacts and likelihood of occurrences of their identified risks.
Tailored Fit
Assessments created according to your organisations needs and Risks.
Get Actionable Reports
Vendor Risk Reports highlighting changes and areas for improvement based on your Assessments.
Leave Contextual Notes
Understand what attributes a risk has, for analysts and others to understand.
Document Findings
Store all your documents, notes and findings related to a vendor in one place!
Additional Evidence
Request additional evidence such as policies and documentation from your Supplier.
Collaboration Built in
A Complete Timeline / Audit Log for each Vendor and their Risk Journey.
STEP THREE
Monitor Live Security Ratings.
Instantly get a snapshot of a Vendors Security Position generated from the computation of over 100,000 Data Points derived from Open Source Intelligence, The Dark web, Commercial & Government Feeds and other sources.
STEP FOUR
Risk Management.
Reduce risk through effective integrated risk management. We help our customers align their strategies with their chosen risk management frameworks and prioritize investments that provide significant ROI.
STEP FIVE
Risk Reporting.
Instantly get a snapshots of a Vendor Security Position generating from the analysis of over 100,000 Data Points derived from Open Source Intelligence, The Dark web, Commercial & Government Feeds and other sources. This data driven visualisation provides an easy to understand risk score based on the changing digital environment.
Simplify supplier assessments and enhance risk management with C2’s ProAssure Services
Case Study Download
Discover how we empowered a global retail client to have greater control and efficiency over their third-party risk

Become a C2 customer today.
Complete the demo request form and a member of our team will be in contact with you.
















